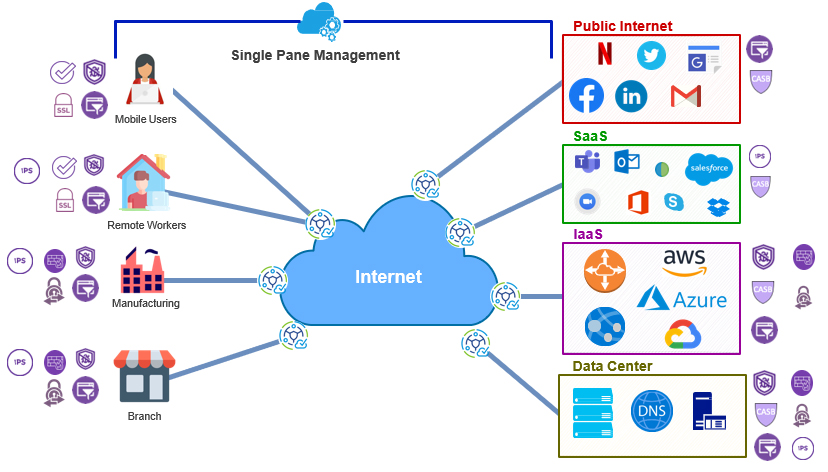
Paradigm Shift: Apply Security Controls to Every User Dynamically Via the Cloud
For businesses with multiple branch offices or locations, the network security landscape is changing rapidly. The broad adoption of Software as a Service (SaaS) applications and cloud services, coupled with remote work and the desire for employees to be able to access applications from anywhere on any device, has increased network risk—at great cost to businesses. According to Fortinet, the average cost of a data breach in 2020 was $3.78 million. Forty-three percent of breaches involved Web applications; with 46% caused by malware distributed by email. Fortinet’s FortiGuard Labs research also shows that the average weekly ransomware activity in June 2021 was more than 10x higher than one year ago–a significant increase in just a 12-month period.
More points of entry to the network, combined with bring-your-own-device initiatives and work from anywhere models, create an ever growing “attack surface.”
Cloud-based security solutions (as opposed to those based on WAN edge, data center, or end-device solutions) can help reduce vulnerability with a scalable, flexible approach that adapts to changes to the business—be it adding employees, deploying technologies, or adopting new devices and applications.
The Cloud Advantage
The ability to apply strong security controls to every user, and do it dynamically via the cloud, is a significant paradigm shift. Previous approaches applied security at the data center, requiring multiple hops to route traffic and causing delays. Premises-based edge devices demand on-site deployment and maintenance of high-compute platforms, and then only protect those locations.
Recently, Hughes executives were invited to speak about securing ever-changing networks amid today’s pervasive threat environment at VMworld, a global conference on digital solutions and networking innovations. Based on our experience delivering this type of solution to customers, we explained how cloud-based solutions enable enterprises to gain persistent detection capabilities strong enough to combat constantly evolving threats, providing users with safe and reliable access to any and all applications, from any location and device.
The Cloud Security/SASE Vision
Such an approach applies security capabilities at the cloud gateway nearest to the user, maintaining the optimal traffic path and avoiding unnecessary hops (which occur each time a data packet is passed from one network node to another). This contrasts with models that apply security via a data center or hosted security service. Fewer hops from a cloud-based application reduce latency and processing delays, improving the user experience.
Security for Sites, Devices and Diners
Delivering security as a service via cloud gateways enables an enterprise to add or modify services, applications and users dynamically at any time via a common management interface. There’s no need to connect into a site and change configurations on security appliances. In the cloud, security software updates or refreshes automatically propagate throughout network, eliminating the time and expense of updating multiple devices or disrupting operations while devices reboot.
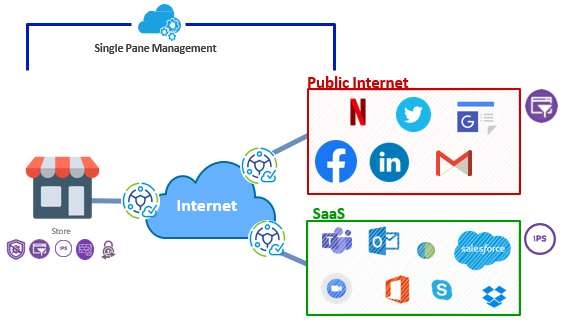
As an example, consider a fast casual restaurant franchise with 300 locations. The enterprise uses SaaS applications for critical business operations with cloud-based security applied at every network entry point.
Hughes Cloud Security in Action: Customer Case Study
- Across the enterprise’s SaaS applications (e.g., MS Outlook, Workday, and POS systems), intrusion detection and prevention systems add to the inherent security provided by the end-to-end SaaS application encryption (which prevents data being read or secretly modified, other than by the true sender and recipient.)
- At the restaurant, next generation Firewall as a Service (FaaS) delivers end point protection for all devices and safeguards customer and payment transaction data through data leak prevention.
- Diners access Guest Wi-Fi to check out the menu, order and pay for meals; cloud-based security measures, including content and URL filtering, protect their personal devices and the network. Similarly, content filtering on the enterprise Wi-Fi system prevents employees from downloading malicious or unauthorized executable files.
Cloud security provides the agility and scalability businesses demand. It is better suited to supporting users working from anywhere and to allowing them access to applications or services located everywhere. By applying the cloud security policies only where needed and orchestrating them across an entire enterprise, even finer levels of control are possible. Best of all, the user experience across the network improves because security is enforced more efficiently for optimized data flow. It’s a new security paradigm that checks all the boxes.