
Managed SASE (Secure Access Service Edge)
Strengthen Your Network and Reduce Costs with Managed SASE
As cyber threats grow and networks become more complex, large enterprises need more than just tools—they need a partner. Hughes Managed SASE delivers 24/7 expert management of your network and security operations, ensuring consistent performance and secure access for your workforce—backed by a trusted leader with deep expertise in managed services, SD-WAN, and designing and deploying network architectures.
SASE Components
Cloud Access Security Broker (CASB)
Keeps your corporate cloud applications and infrastructure safe from cyber attacks, shadow AI, and data leaks with advanced data loss prevention (DLP) capabilities.
Next Generation Secure Web Gateway (NG-SWG)
Blocks malicious applications and websites and prevents unsecured internet traffic from entering your internal network.
Firewall-as-a-Service (FWaaS)
Inspects and protects network traffic against threats and helps enforce security policies consistently across your network.
Zero Trust Network Access (ZTNA)
Eliminates inherent trust, requiring strong, regular identity-based authentication and authorization of devices and users.
Software-Defined Wide Area Network (SD-WAN)
Helps make your internet connections faster, more reliable, and efficient. An affordable way to connect your organization with branch offices and store locations.
The Building Blocks of Hughes Managed SASE
Hughes Managed SASE gives your workforce secure, frictionless access wherever they are—backed by AI-driven threat defense, Zero-Trust security, and centralized policies. With integrated SD-WAN and digital experience monitoring, it streamlines anagement, improves user experience, and keeps your data protected.

Expert-Led Centralized Management
Hughes partners with your team to simplify the deployment and management of your network and security systems. We reduce complexity, standardize, and streamline operations and manage your complex ecosystem of vendors and tools with our 24×7 support.

Optimized Network Performance
Designed for mid to large enterprises with diverse infrastructures, our experts help you streamline operations, resolve issues faster, and cut costly downtime—so your workforce always benefits from optimized network performance and connectivity.

Secure Access From Anywhere
From branch to HQ to remote teams, your workforce gets secure, reliable Zero-Trust access to all your cloud-based applications, while your IT security team gets the visibility, control, and support they need to focus on your business.
Benefits of Hughes Managed SASE
| Benefit | Solution |
| Drive business growth and digital transformation | Through a consultative partnership, we help you stay agile and competitive with innovative technology that’s financially sound and aligned with your strategic business objectives. |
| Reduce business and financial risk | We help you establish a culture of security and accountability, enforcing policies, safeguarding sensitive data, and implementing GenAI governance that preserves trust and protects your brand. |
| Lower costs and improve ROI | We transform technology investments into strategic advantages, reducing total cost of ownership, speeding execution, and realizing business value faster. |
| Strengthen network security and performance | We provide expert oversight of both network and security operations, backed by exceptional engineering and cybersecurity expertise, and superior vendor consolidation, management, and oversight capabilities. |
| Improve IT security staff efficiency | Our experts partner with your team to ease operational load through automation, insights, and a 24/7 Security Operation Center (SOC), so your team can focus on driving your business initiatives forward. |
| Enhance workforce productivity | We use established Zero Trust principles that provide your workforce with seamless, consistent, and secure access to cloud applications and enterprise resources, regardless of where they connect from. |
Why Hughes?
Today’s large enterprises demand always-on network connectivity, stronger security, and scalable performance—across every location, user, and device. But keeping pace with evolving threats, cloud adoption, and growing infrastructure challenges isn’t easy.
That’s where Hughes comes in.

An Expert by Your Side
With over 30 years of experience as a Managed Services Provider (MSP), and deep-rooted expertise in SD-WAN and cybersecurity, Hughes has the people, skills, and resources to keep your network running safe and strong.

A Trusted Global Leader
Recognized by Gartner® as a Managed Network Services Leader, Hughes is your trusted partner, committed and accountable for both network and security operations to reduce complexity, streamline operations, and stay secure.
Network Experience
30+ years of experience as a Managed Services Provider
Deep-rooted expertise in SD-WAN, and managing network connectivity, performance, and reliability
Over 95,000 SD-WAN sites rely on our support
Comprehensive, scalable, multi-layer approach to network and cybersecurity management

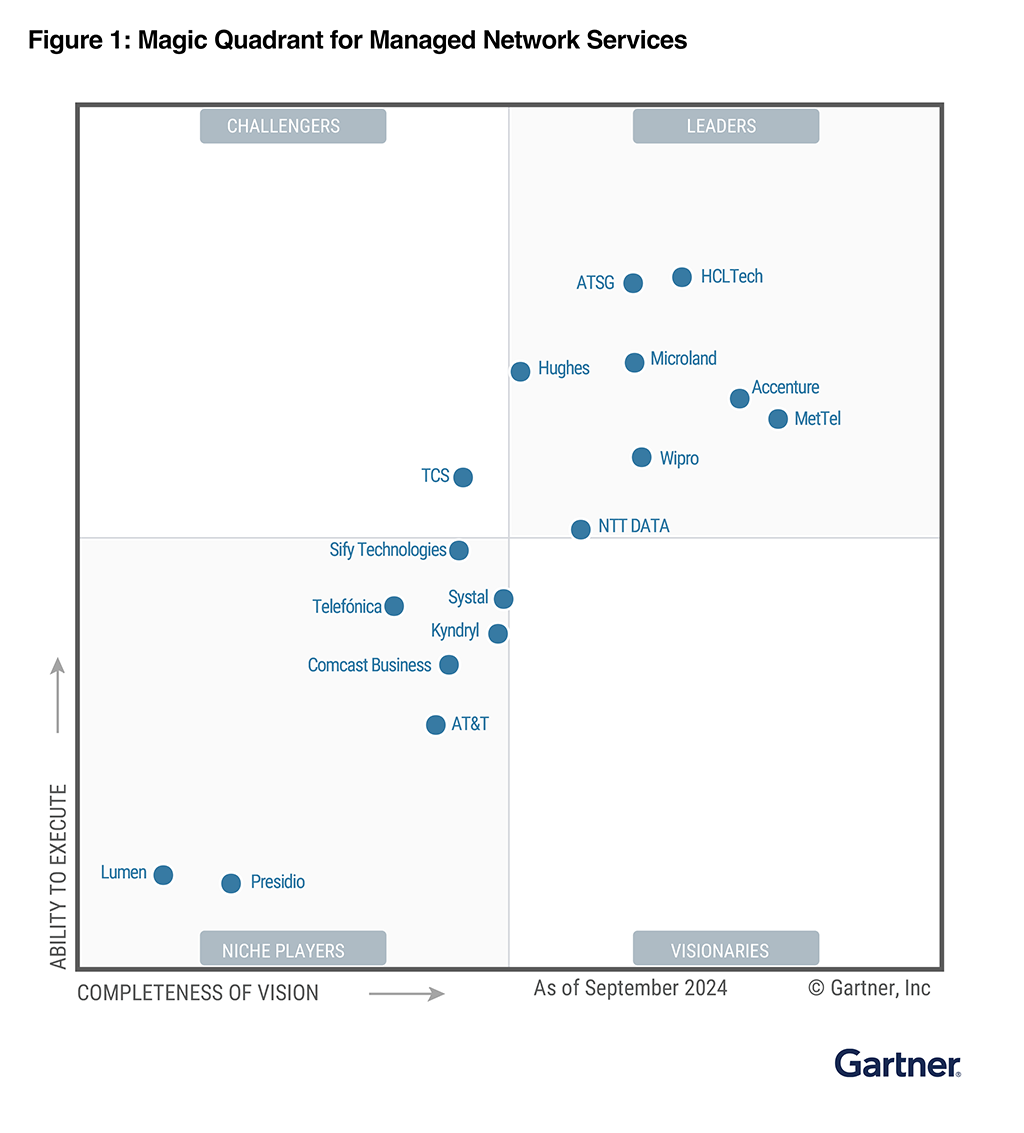
Industry Recognition
A Gartner® Magic Quadrant™ Leader for Managed Network Services for two consecutive years
Gartner Peer Insights™ overall rating of 4.6/5, recommended by 87% for Managed Network Services*
CyberSecurity Breakthrough as 2024 MSSP of the Year
Frost & Sullivan as a six-time leader in Frost Radar™ for Managed SD-WAN Services
Tech Ascension 2025 Best Managed Services Provider for Managed SASE
Cybersecurity Expertise
Exceptional engineering and qualified staff to deploy, migrate, and manage the SASE solution
Superior products from best-in-class partners, fully deployed and managed solution
Deep consulting and design expertise in building solid security adoption roadmap and risk mitigation strategies


Proven Best Practices
Day 1 implementation, migration, and adoption framework with achievable timelines
Day 2 best practices ensure consistent quality of service for production operations and change management
Superior vendor consolidation, management, and oversight capabilities
Offerings customized with customer-focused timelines, flexible pricing, and no overspending
Best-in-Class Partnerships
Hughes partners with industry-recognized SASE leaders.

Built on an industry-leading SD-WAN and a global network of Points of Presence, Netskope delivers advanced data loss prevention that integrates with a vast array of applications, and the strongest Zero Trust architecture—ensuring fast, secure access to AI, cloud, and web at the edge.

With 20+ years of experience and over 1,500 active FortiSASE enterprise customers, Fortinet stands out for their superior SD-WAN and firewall capabilities. It’s the only SASE platform to support seamless integration with Wireless Access Points and Wi-Fi extenders.
With Hughes, your teams stay connected and productive—while your data stays protected.
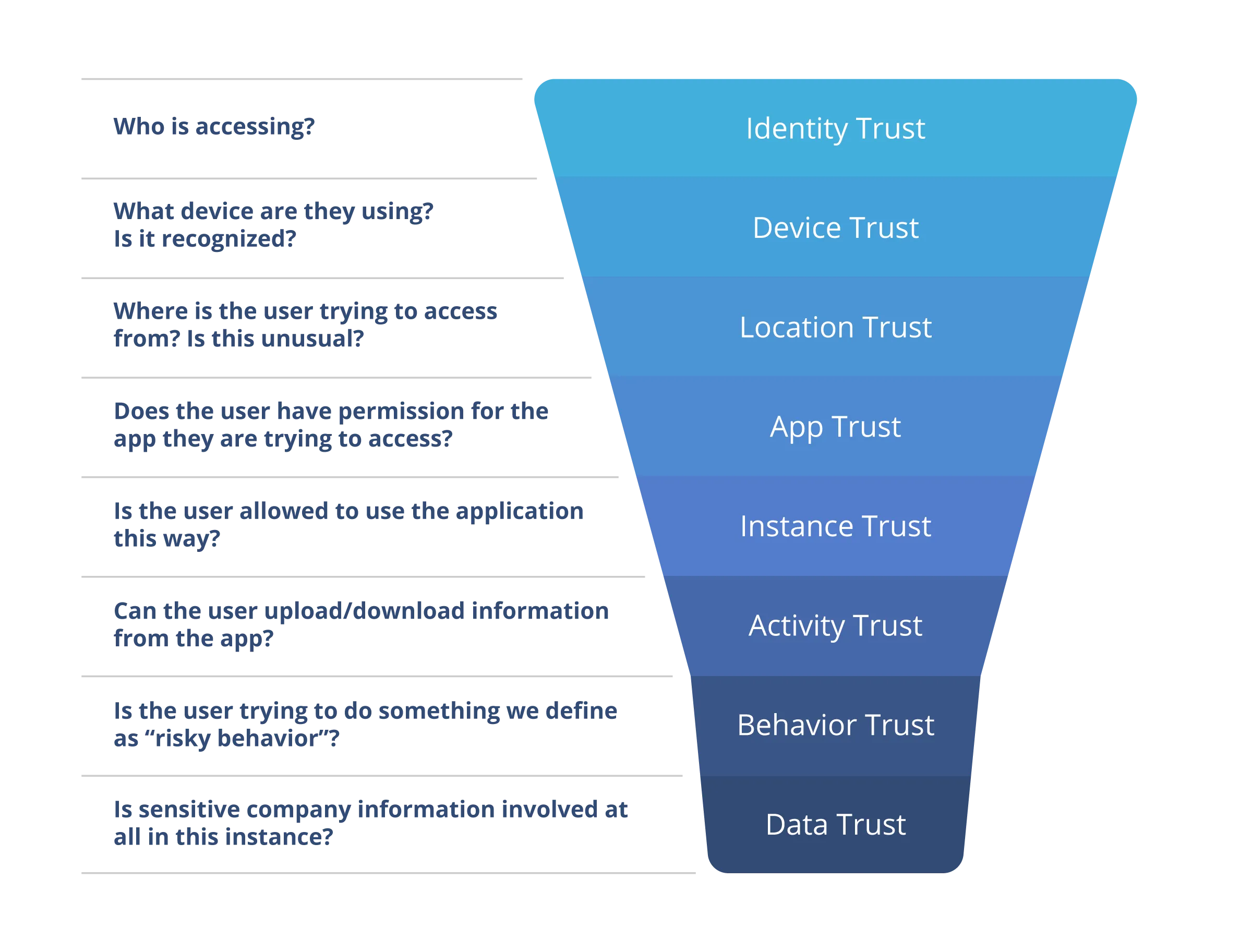
Zero Trust Principles
Hughes Managed SASE applies Zero Trust principles in real-time to authenticate and authorize every user interaction across the enterprise edge.
Failed validations deny access and generate alerts. Real-time policy enforcement, threat detection, and adaptive access controls ensure secure connectivity.
Through active user coaching, future risky behavior can be mitigated dramatically.

Data Loss Prevention
Integrated into the SASE framework, advanced Data Loss Prevention enforces data protection policies and stops exfiltration of sensitive data from your business – across outbound email, websites, SaaS/IaaS, CRM and other commonly used applications.
DLP detects and blocks unauthorized sharing of sensitive information in real time, ensuring compliance and preventing data from leaving your network without explicit approval.
*as of December 2025 based on 69 reviews
