Every Path. Every Cloud. Everywhere.
A vulnerability anywhere is a risk everywhere. We deliver managed cybersecurity designed to defend everywhere our clients go and every way their network grows. We plug the gaps traditional cybersecurity vendors don’t, defending every transport type, including satellite, cellular, microwave and the connections highly distributed enterprises depend on.
Accelerating Big Ideas Without Big Budgets (Or Big Headaches)
At Hughes, we give highly distributed enterprises the freedom to grow. We help emerging businesses move beyond smaller solutions or home-brew defense to tailored enterprise-grade protection without having to build it themselves. Get 24X7 monitoring with SOC-as-a-service, so a team of cybersecurity experts are always watching your business.
Expertise That Drives Sales
The goal of cybersecurity should be better business, not just better cybersecurity. At Hughes, we focus on practical cybersecurity designed for highly distributed enterprises. With the expertise of more than four decades managing many of the most successful distributed retailers, hospitality, restaurants, QSR, gas stations and others, we understand how to optimize cybersecurity while optimizing commercial network performance.
Business Without Boundaries
We deliver managed cybersecurity services that make cybersecurity a foundation of your business, not just a perimeter defense, so every next goal has a secure path to reach it. We work alongside you as a business partner, to provide tailored solutions best aligned to your goals. Wherever your business goes, or however complex it grows, Hughes managed cybersecurity helps define the path and secure the way.
Hughes is more than just a provider. We are your partner - helping you achieve your strategic goals. Contact us to learn more.
Hughes Recognized as a Leader
MSSP Alert Named to Top 250 MSSP List for 4 years
Identified as a Leader in the Frost Radar™: Managed SD-WAN Services in North America for 5 consecutive years
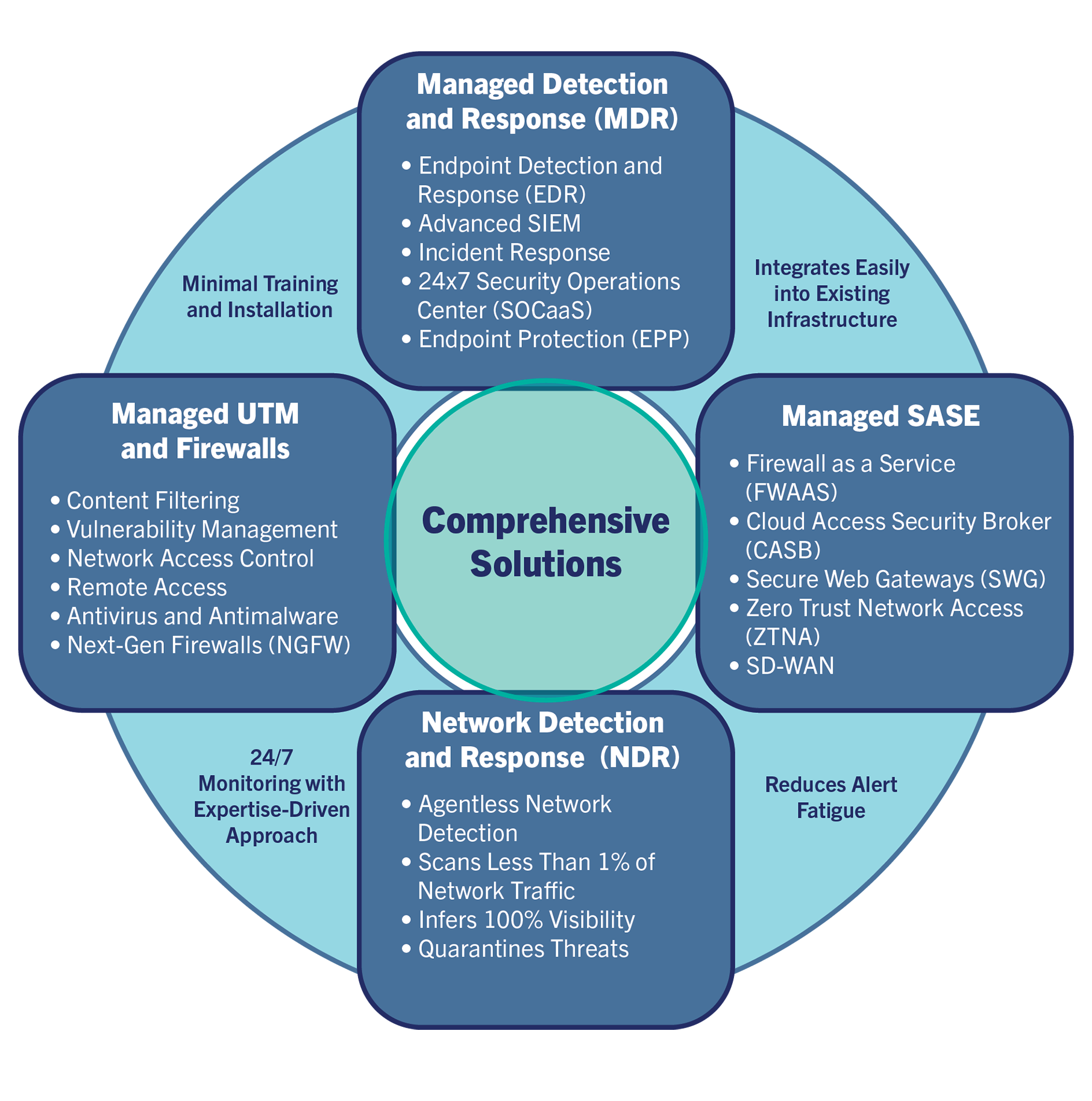
Hughes focuses on practical cybersecurity solutions designed explicitly for highly distributed enterprises. Make cybersecurity a foundation of your business, not just a perimeter defense.
- Managed Secure Access Service Edge (SASE)
- Managed Unified Threat Management (UTM)
- Managed Detection & Response (MDR)
- Ransomware & Zero-Day Prevention
- Network Detection and Response (NDR)
With Hughes, you can defend your business against emerging cyber threats, simplify your security infrastructure, and stay ahead in an ever-changing digital landscape. Don't wait until a cyberattack happens—contact us today to learn more about how our managed security services can safeguard your business and drive your success.
Video Resources
Essential Cybersecurity Resources

Through advanced AI and Deep Learning, Hughes protects customers from zero-days and ransomware with industry leading efficiency.

Discover trends, challenges, and strategies shaping secure networks in 2025, based on insights from 400+ IT leaders.

A complete Buyer's Guide for enterprises evaluating NDR Solutions. Includes core capabilities of NDR, how to select the right NDR solution, NDR Buyer...

How an MNSP can help you implement proactive measures to stay ahead of cybersecurity challenges.







Learn more about the details behind Hughes Ransomware and Zero-Day prevention and how it protects from modern cyber threats.

The increasing interest around SASE has uncovered a trend in the networking and security world that highlights the need for secure access solutions...