Managed NAC | Network Access Control | Hughes
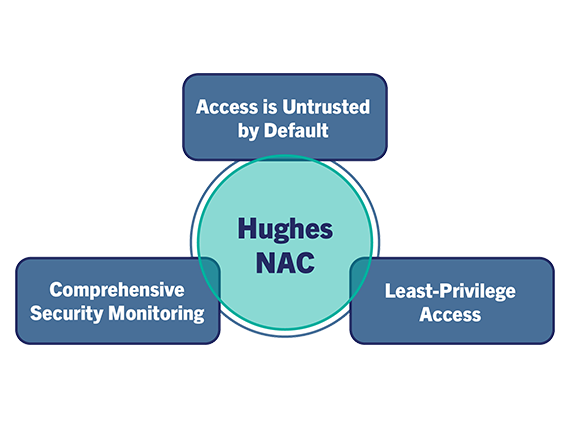
Hughes delivers a modern Network Access Control (NAC) solution that empowers you to confidently secure your network environment. Built with zero trust principles, Hughes provides the visibility, control, and automation you need to effectively manage and secure every device seeking access.
Network Access Control and Security
Hughes meticulously identifies, validates, and governs every connection attempting to access the network, whether it’s a wired or wireless connection. This solution leverages a multifaceted approach, utilizing data from diverse sources and analyzing device behavior to achieve a granular understanding of all network participants. Additionally, Hughes identifies all of the devices attempting to connect to your network, and enforces granular, role-based access policies. This safeguards critical data and sensitive assets while ensuring adherence to all relevant industry regulations and established security standards.
NAC functionality ensures that only successfully authenticated endpoints are authorized in the production network. Adhering to “Need to know” & “Separation of duties” security principles often found in zero trust policies.
- Devices connected to ports with the NAC function enabled are put into an onboarding VLAN
- The onboarding VLAN has a restrictive security policy, device identification enabled, a DHCP server, and a captive portal enabled
- The device identification feature collects device information. When the device matches the patterns that are defined in a NAC policy, an action is applied to the device, such as moving it to a specific VLAN or having a security policy applied.
Pre-Connection Validation and Ongoing Monitoring
Upon a device attempting to join the network, Hughes rigorously validates its configuration against established compliance criteria. If discrepancies are detected, the connection is either denied outright, or the device is isolated within a limited-access VLAN. Users are promptly notified of any non-compliance issues and the need for corrective action. Access is only granted once the device configuration has been successfully remediated. This multi-layered approach guarantees a secure and compliant network environment.
Incident Response
As a part of comprehensive Cyber Security strategy, the NAC function can be leveraged as an Incident Response function for the identified cyber threats in the production environment that warrant immediate attention.
Why Hughes?
Hughes goes beyond traditional NAC solutions, offering a feature-rich platform that delivers exceptional value:
- Advanced Threat Detection with AI: Leverage Hughes industry-leading artificial intelligence (AI) to identify anomalous device behavior and potential threats that might slip past traditional NAC solutions.
- Extensive Automation: Simplify security operations with extensive automation capabilities. Hughes automates workflows for device onboarding, access control enforcement, and threat response, saving you valuable time and resources.
- Deployment Flexibility: Hughes caters to diverse network configurations. It offers centralized management for large deployments and flexible options for distributed networks, ensuring scalability for businesses of all sizes
Hughes: Benefits at a Glance
Unmatched Visibility:
Gain comprehensive insights into all connected devices, including wired, wireless, IoT, and guest users. Hughes asset inventory helps you identify unknown devices and potential vulnerabilities.
Automated Threat Response:
Hughes automates responses to security incidents. Isolate suspicious devices, block malware, and take swift action to minimize the impact of potential threats.
Reduced Security Risks:
By proactively identifying and managing device vulnerabilities, Hughes helps you significantly reduce your network’s exposure to security risks like malware attacks and data breaches.
Simplified BYOD and Guest Management:
Hughes streamlines Bring Your Own Device (BYOD) and guest user management. Enforce security policies for BYOD devices and provide secure, controlled access for guest users.
Granular Access Control:
Implement role-based access controls to restrict or grant access based on device type, user identity, and security posture. This ensures only authorized devices with appropriate security hygiene can access your network resources.